Abstract
LS-designs are a family of bitslice ciphers aiming at efficient masked implementations against side-channel analysis. This paper discusses their security against invariant subspace attacks, and describes an alternative family of eXtended LS-designs (XLS-designs), that enables additional options to prevent such attacks. LS- and XLS-designs provide a large family of ciphers from which efficient implementations can be obtained, possibly enhanced with countermeasures against physical attacks. We argue that they are interesting primitives in order to discuss the general question of “how simple can block ciphers be?”.



Similar content being viewed by others
Notes
As just mentioned, this attack can be applied by finding an invariant subspace for the linear layer as well, in which case the S-box layer will not change the subspace.
More precisely, three ANDs and one OR, which can be masked at the same cost.
Any S-box has (small dimensional) subspaces that gets mapped to subspaces.
For more constrained space, they could be computed as suggested in Sect. 3.1.
References
Albrecht M.R., Driessen B., Kavun, E.B., Leander G., Paar C., Yalçin T.: Proceedings on Block ciphers—focus on the linear layer (feat. PRIDE) Part I. In: Garay J.A., Gennaro R. (eds.) Advances in Cryptology—CRYPTO 2014—34th Annual Cryptology Conference, Santa Barbara, 17–21 Aug, 2014. Lecture Notes in Computer Science, vol. 8616, pp. 57–76. Springer, Berlin (2014).
Albrecht M.R., Rechberger C., Schneider T., Tiessen T., Zohner M. Ciphers for MPC and FHE. In: Oswald, E., Fischlin M (eds.): Proceedings on Advances in Cryptology—EUROCRYPT 2015—34th Annual International Conference on the Theory and Applications of Cryptographic Techniques Part I, Sofia, 26–30 Apr 2015, pp. 430–454. Lecture Notes in Computer Science, vol. 9056. Springer, Berlin (2015)
Augot D., Finiasz M.: Direct construction of recursive MDS diffusion layers using shortened BCH codes. In: Cid C., Rechberger C. (eds.): Fast Software Encryption-21st International Workshop, FSE 2014, 3–5 London, 2014, Revised Selected Papers, pp. 3–17. Lecture Notes in Computer Science, vol. 8540, Springer, Berlin (2015).
Biryukov A., De Cannière C.: Block ciphers and systems of quadratic equations. In: Johansson T. (ed.) Fast Software Encryption, 10th International Workshop, FSE 2003, Lund, 24–26 Feb, 2003, Revised Papers. Lecture Notes in Computer Science, vol. 2887, pp. 274–289. Springer, Berlin (2003).
Bogdanov A., Knudsen L.R., Leander G., Standaert F.-X., Steinberger, J.P., Tischhauser E.: Key-alternating ciphers in a provable setting: encryption using a small number of public permutations—(extended abstract). In: Pointcheval D., Johansson T. (eds.) Proceedings on Advances in Cryptology—EUROCRYPT 2012—31st Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, 15–19 Apr 2012. Lecture Notes in Computer Science, vol. 7237, pp. 45–62. Springer, Berlin (2012).
Boura C., Canteaut A.: Zero-sum distinguishers for iterated permutations and application to Keccak-f and Hamsi-256. In: Biryukov A., Gong G., Stinson D.R. (eds.) Selected Areas in Cryptography—17th International Workshop, SAC 2010, Waterloo, 12–13 Aug 2010, Revised Selected Papers. Lecture Notes in Computer Science, vol. 6544, pp. 1–17. Springer, Berlin (2010).
Boura C., Canteaut A. De Cannière C.: Higher-order differential properties of Keccak and Luffa. In: Joux A. (ed.) FSE. Lecture Notes in Computer Science, vol. 6733, pp. 252–269. Springer, Berlin (2011).
Chari S., Jutla C.S., Rao J.R., Rohatgi P.: Towards sound approaches to counteract power-analysis attacks. In: Wiener M.J. (ed.) Proceedings on Advances in Cryptology—CRYPTO ’99, 19th Annual International Cryptology Conference, Santa Barbara, 15–19 Aug 1999. Lecture Notes in Computer Science, vol. 1666, pp. 398–412. Springer, Berlin (1999).
Courtois N., Pieprzyk J.: Cryptanalysis of block ciphers with overdefined systems of equations. In: Zheng Y. (ed.) Proceedings on Advances in Cryptology—ASIACRYPT 2002, 8th International Conference on the Theory and Application of Cryptology and Information Security, Queenstown, 1–5 Dec 2002. Lecture Notes in Computer Science, vol. 2501, pp. 267–287. Springer, Berlin (2002).
Daemen J., Rijmen V.: The wide trail design strategy. In: Honary B. (ed.) Proceedings on Cryptography and Coding, 8th IMA International Conference, Cirencester, 17–19 Dec 2001. Lecture Notes in Computer Science, vol. 2260, pp. 222–238. Springer, Berlin (2001).
Daemen J., Rijmen V.: Information Security and Cryptography. The Design of Rijndael: AES—The Advanced Encryption Standard. Springer, Berlin (2002)
Daemen J., Knudsen L.R., Rijmen V.: The block cipher Square. In: Biham E. (ed.) Proceedings on Fast Software Encryption, 4th International Workshop, FSE ’97, Haifa, 2–22 Jan 1997. Lecture Notes in Computer Science, vol. 1267, pp. 149–165. Springer, Berlin (1997).
Daemen J., Peeters M., Van Assche G., Rijmen V.: Nessie proposal: the block cipher Noekeon. Nessie submission (2000). http://gro.noekeon.org/.
Dinur I., Shamir A.: Cube attacks on tweakable black box polynomials. In: Joux A. (ed.) Proceedings on Advances in Cryptology—EUROCRYPT 2009, 28th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cologne, 26–30 Apr 2009. Lecture Notes in Computer Science, vol. 5479, pp. 278–299, Springer, Berlin (2009).
Galice S., Minier M.: Improving integral attacks against Rijndael-256 up to 9 rounds. In: Vaudenay S. (ed.) Proceedings on Progress in Cryptology—AFRICACRYPT 2008, First International Conference on Cryptology in Africa, Casablanca, 11–14 Jun 2008. Lecture Notes in Computer Science, vol. 5023, pp. 1–15. Springer, Berlin (2008).
Gérard B., Grosso V., Naya-Plasencia M., Standaert, F.-X.: Block ciphers that are easier to mask: How far can we go? In: Bertoni G., Coron J.-S. (ed.) Proceedings on Cryptographic Hardware and Embedded Systems—CHES 2013—15th International Workshop, Santa Barbara, 20–23 Aug 2013. Lecture Notes in Computer Science, vol. 8086, pp. 383–399. Springer, Berlin (2013).
Gilbert H., Peyrin T.: Super-sbox cryptanalysis: improved attacks for AES-like permutations. In: Hong S., Iwata T. (eds.) Fast Software Encryption, 17th International Workshop, FSE 2010, Seoul, 7–10 Feb 2010, Revised Selected Papers. Lecture Notes in Computer Science, vol. 6147, pp. 365–383. Springer, Berlin (2010).
Grosso V., Leurent G., Standaert F.-X., Varici K.: LS-designs: Bitslice encryption for efficient masked software implementations. In: Cid C., Rechberger C. (eds.): Fast Software Encryption—21st International Workshop, FSE 2014, 3–5 London, 2014, Revised Selected Papers, pp. 18–37. Lecture Notes in Computer Science, vol. 8540, Springer, Berlin (2015).
Guo J., Peyrin T., Poschmann A. Robshaw M.: The LED block cipher. In: Preneel B., Takagi T. (eds.) Proceedings on Cryptographic Hardware and Embedded Systems—CHES 2011—13th International Workshop, Nara, Sep 28–1 Oct 2011. Lecture Notes in Computer Science, vol. 6917, pp. 326–341. Springer, Berlin (2011).
Knudsen L.R.: Truncated and higher order differentials. In: Preneel, B. (ed.) Proceedings on Fast Software Encryption: Second International Workshop, Leuven, 14–16 Dec 1994. Lecture Notes in Computer Science, vol. 1008, pp. 196–211. Springer, Berlin (1994).
Knudsen L.R., Leander G., Poschmann A., Robshaw M.J.B.: Printcipher: a block cipher for ic-printing. In: Mangard S., Standaert F.-X. (eds.): Proceedings on Cryptographic Hardware and Embedded Systems, CHES 2010, 12th International Workshop, Santa Barbara, 17–20 Aug 2010, pp. 16–32. Lecture Notes in Computer Science, vol. 6225, Springer, Berin (2010).
Knudsen L.R., Wagner D.: Integral cryptanalysis. In: Daemen J., Rijmen V. (eds.) Fast Software Encryption, 9th International Workshop, FSE 2002, Leuven, 4–6 Feb 2002, Revised Papers. Lecture Notes in Computer Science, vol. 2365, pp. 112–127. Springer, Berlin (2002).
Leander G., Abdelraheem M.A., AlKhzaimi H., Zenner E.: A cryptanalysis of PRINTcipher: the invariant subspace attack. In: Rogaway P. (ed.) Proceedings on Advances in Cryptology—CRYPTO 2011—31st Annual Cryptology Conference, Santa Barbara, 14–18 Aug 2011. Lecture Notes in Computer Science, vol. 6841, pp. 206–221. Springer, Berlin (2011).
Leander G., Minaud B, Rønjom S.: A generic approach to invariant subspace attacks cryptanalysis of Robin, iSCREAM and Zorro. To Appear in the Proceedings of EUROCRYPT 2015 (2015).
Leander G., Minaud B., Rønjom S.: A generic approach to invariant subspace attacks: cryptanalysis of Robin, iSCREAM and zorro. In: swald, E., Fischlin M (eds.): Proceedings on Advances in Cryptology—EUROCRYPT 2015—34th Annual International Conference on the Theory and Applications of Cryptographic Techniques Part I, Sofia, 26–30 Apr 2015, pp. 254–283. Lecture Notes in Computer Science, vol. 9056, Springer, Berlin (2015).
Minier M., Phan R.C.-W., Pousse B.: On integral distinguishers of Rijndael family of ciphers. Cryptologia 36(2), 104–118 (2012).
Piret G., Roche T., Carlet C.: PICARO—a block cipher allowing efficient higher-order side-channel resistance—extended version-IACR Cryptology ePrint Archive 2012, 358 (2012)
Rivain M., Prouff E.: Provably secure higher-order masking of AES. In: Mangard S., Standaert F.-X. (eds.): Proceedings on Cryptographic Hardware and Embedded Systems, CHES 2010, 12th International Workshop, Santa Barbara, 17–20 Aug 2010, pp. 413–427. Lecture Notes in Computer Science, vol. 6225, Springer, Berin (2010).
Todo Y.: Structural evaluation by generalized integral property. In: Oswald, E., Fischlin M (eds.): Proceedings on Advances in Cryptology—EUROCRYPT 2015—34th Annual International Conference on the Theory and Applications of Cryptographic Techniques Part I, Sofia, 26–30 Apr 2015, pp. 287–314. Lecture Notes in Computer Science, vol. 9056, Springer, Berlin (2015).
Ullrich M., De Cannière C., Indesteege S., Küçük Ö., Mouha N., Preneel B.: Finding optimal bitsliced implementations of 4\({\times }\)4-bit s-boxes. In: SKEW 2011 Symmetric Key Encryption Workshop, Copenhagen, pp. 16–17 (2011)
Wagner D.: The boomerang attack. In: Lars R.K. (ed.) Proceedings on Fast Software Encryption, 6th International Workshop, FSE ’99, Rome, 24–26 Mar 1999. Lecture Notes in Computer Science, vol. 1636, pp. 156–170. Springer, Berlin (1999).
Acknowledgments
François-Xavier Standaert Standaert is a research associate of the Belgian Fund for Scientific Research (FNRS-F.R.S.). This work has been funded in parts by the Brussels Region INNOVIRIS project SCAUT, and by the European Commission through the ERC Project 280141 (CRASH).
Author information
Authors and Affiliations
Corresponding author
Additional information
This is one of several papers published in Designs, Codes and Cryptography comprising the “Special Issue on Coding and Cryptography”.
Appendices
Appendix: Specifications of \(\mathsf {Mysterion}\)’s components
1.1 \(\mathsf {Mysterion}\) S-box

1.2 \(\mathsf {Mysterion}\) L-box
C is the companion matrix of the polynomial defined in Sect. 4.1. \(C^8\) is the underlying matrix of the \(\mathsf {Mysterion}\) \(\mathsf {L}\)-box.
1.3 \(\mathsf {ShiftColumns}\) of Mysterion-256
Proofs for the bound of the number of active \(\mathsf {S}\)-boxes
Proof of Theorem 2
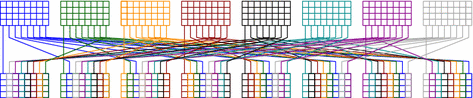
The internal state of Mysterion-256 can be seen as a square, since the number of blocks is equal to the number of columns in a block in this case. Therefore, the proof directly results from the Four-Round Propagation Theorem of the AES Rijndael given in [10]. That is, the number of active S-boxes over four rounds of Mysterion-256 is lower bounded by the square of the branch number of the \(\mathsf {L}\)-box, which corresponds to \(9^2 = 81\) active \(\mathsf {S}\)-boxes (See Fig. 4).\(\square \)
Proof of Theorem 1
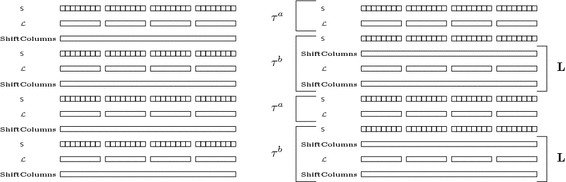
Contrary to Mysterion-256, we cannot directly use the Four-Round Propagation Theorem of the AES to lower bound the number of active S-boxes in Mysterion-128, since its number of columns is larger than its number of blocks (i.e. the state is no longer a square). However, similar bounds can be deduced from a modified version of the theorem proven in [10]. We show in the following how Mysterion-128 can fulfill the hypotheses of this theorem with a simple rearrangement of its operations. For this purpose, we first need to set some definitions and notations. First, a bundle is a 4-bit word and corresponds to a column in the representation of the internal state of Mysterion-128. We denote by \(\mathcal {L}\) the application of the \(\mathsf {L}\)-box on each block of the state, which are divided into four independent parts of eight bundles each. We call this partition of the bundles \(\Xi \). Mysterion-128 is a key-alternating block cipher and iteratively applies the same round function, composed of an \(\mathsf {S}\)-box layer, an \(\mathsf {L}\)-box layer, a \(\mathsf {ShiftColumns}\) layer, and key and round constant additions. As the latter do not influence the number of active S-boxes, we will omit them in the following. Based on this, four rounds of Mysterion-128 can then be written as:
We next reorganise these operations in order to highlight a particular structure of the linear transformation for 4 rounds, which allows a simpler analysis. More precisely, since \(\mathsf {ShiftColumns}\) commutes with \(\mathsf {S}\), we have the following equivalent definition of four rounds of Mysterion-128:
Thanks to this representation, we easily identify two different transformations \(\tau ^a = \mathcal {L} \circ S\) and \(\tau ^b = \mathbf {L} \circ S\), where \(\mathbf {L} = \mathsf {ShiftColumns} \circ \mathcal {L} \circ \mathsf {ShiftColumns}\). Then four rounds of Mysterion-128 are the alternation of \(\tau ^a\) and \(\tau ^b\):
Figure 5 summarizes our notations and modified representation of Mysterion-128.\(\square \)
We finally exploit the following theorem from [10]:
Theorem 3
For a key alternating block cipher with round tranformations \(\tau ^a\) and \(\tau ^b\), the number of active S-boxes of any trail over
is lower bounded by \(\mathcal {B}(\mathcal {L}) \times \mathcal {B}(\mathbf {L},\Xi )\), where \(\mathcal {B}(\mathcal {L})\) is the branch number of the linear transformation \(\mathcal {L}\) and \(\mathcal {B}(\mathbf {L},\Xi )\) is the branch number of the linear transformation \(\mathbf {L}\) with respect to the partition of the bundles \(\Xi \).
The branch number of \(\mathcal {L}\) is 9 (the \(\mathsf {L}\)-box of \(\mathsf {Mysterion}\) is an MDS code \([16,8,9]_{\mathbb {F}_{2^4}}\)). The partition \(\Xi \) divide the state into the 4 blocks. We say a block is active when it has at least one active (i.e non zero) bundle. As the \(\mathsf {ShiftColumns}\) operation spreads two bundles of each block into other blocks, and as \(\mathcal {L}\) is MDS, we have that the minimum number of input/output active blocks, therefore the branch number of \(\mathbf {L}\) with respect to the partition \(\Xi \), is 5. As a result, the number of active S-boxes over four rounds is lower bounded by \(9\times 5 = 45\).
Rights and permissions
About this article
Cite this article
Journault, A., Standaert, FX. & Varici, K. Improving the security and efficiency of block ciphers based on LS-designs. Des. Codes Cryptogr. 82, 495–509 (2017). https://doi.org/10.1007/s10623-016-0193-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10623-016-0193-8